We talk a lot about cybersecurity in the OT space. Cybersecurity has always posed a unique challenge for OT technologies, for a number of reasons. Often, OT teams are dealing with legacy technology that was never designed to be cybersecure and doesn’t operate in a...

Posts by or with Alexandre Peixoto
What Type of Cyber Defender Is Your OT Team?
We’ve talked a lot in this space about how cybersecurity is a particularly difficult challenge for OT teams. For decades, OT systems were specifically engineered to be closed to the outside world and from one another to ensure secure, reliable operation. That trend...
Unraveling the Cybersecurity Knot: How OT Teams Can Leverage Automation Experts
It has become increasingly obvious that the need for strong cybersecurity is not going to go away. Operational technology (OT) assets have increasingly become targets of both large-scale and small-scale attacks, often with devastating effects. OT teams need to be...
Industrial Cybersecurity Navigates a New Normal
Cybersecurity is a critical concern for industrial manufacturers these days, particularly as high-profile incidents targeting plants have become the new normal. No organization wants to risk the production loss, safety concerns, and reputation damage that come with a...
Cybersecurity Strategies for the Rise of Next-Gen Automation
Today’s most successful organizations are facing a wide variety of new challenges: a need for increased flexibility, a push toward more sustainable operations, a shrinking experienced workforce, and more. Meeting those challenges will require unlocking the next...
Make the Cybersecurity Journey Far Less Puzzling
Tackling cybersecurity can often feel like trying to complete an overly complex jigsaw puzzle. Figuring out how all the pieces connect is often a frustrating step. In the worst cases, however, the cybersecurity jigsaw puzzle doesn’t even have edges. And when that...
Expanding Cybersecurity Offerings to Meet a Future of Boundless Automation
One of the most obvious changes in process manufacturing in the last decade has been a move toward more connected, integrated operations. A key component of this change, in fact, has been a recent trend by operations teams to accommodate more cloud and internet...
Five Things You Can Do, Starting Today, to Improve Your Cybersecurity Defenses
Recent world events—from the expansion of remote access in response to COVID restrictions to high-profile industrial cyberattacks—have put a renewed focus on cybersecurity. While cybersecurity needs vary from organization to organization, there are common, critical...
Three Things to Do, and Three to Avoid, When Assessing Your Cybersecurity Situation
Any process manufacturing company that has not yet launched a cybersecurity program is probably frozen in a frequent difficult position: Where do we start? If your company is trying to break free and make some progress—and maybe you’re the one tasked with doing it—we...
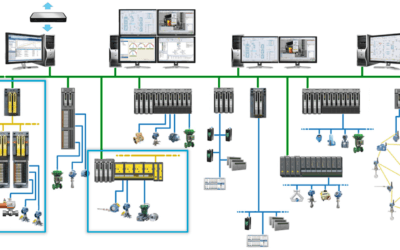
Selecting the Right Automation Architecture
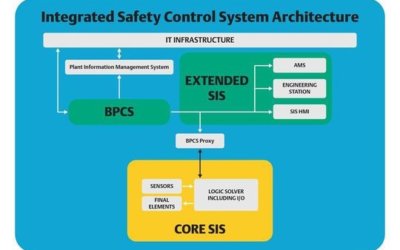
Creating a safe and secure automation process starts with implementing a well-designed basic process control system (BPCS) and safety instrumented system (SIS). Government agencies and industry associations offer guidelines and requirements for how these systems...
Successful Remote Connectivity Strategies Start with Cybersecurity
Industrial manufacturing organizations have faced several challenges in the last few years. Perhaps the biggest change has been the need for personnel to perform critical tasks from outside the plant. This move toward more remote work has likely spurred more recent...
Cybersecurity Considerations for Automation Architectures
In an Industrial Safety and Security Source article, Considerations in Choosing a Defendable Safety System Architecture, Emerson’s Sergio Diaz and Alexandre Peixoto focus on the basic process control system (BPCS) and safety instrumented system (SIS). They compare various architectures from a cybersecurity perspective.
Our Global Community
Emerson Exchange 365
The opinions expressed here are the personal opinions of the authors. Content published here is not read or approved by Emerson before it is posted and does not necessarily represent the views and opinions of Emerson.