Savannah River’s Greg Stephens and Emerson’s Randy Pratt present, DeltaV Security – Don’t Let Your Business Be Caught Without It at the recent Emerson Exchange conference in Nashville.
[slideshare id=10012916&doc=deltav-security-dont-let-your-business-be-caught-without-it-111103133851-phpapp02]
They opened noting cyber security risks change rapidly and most process manufacturers know they need to be secure. There’s a feeling that few really know how to assess and address these risks. The key is to strive for a solid strategy that has effective actions. Communicating the risks in business terms is crucial to the execution of the strategy.
There is a lot of fear of the unknown with respect to cyber-security. With the arrival of Stuxnet, Night Dragon, Duqu, etc. these worries are no longer abstract. Process manufacturers’ control systems are productivity tools and contain a large portion of their intellectual property. For some industries, regulatory agencies have standards describing what risk mitigation is required.
Greg and Randy provided some basic tools and terms around cyber security risk assessment. Vulnerability is a flaw or weakness that may lead to an undesired consequence. Risk is the characterization of the likelihood and severity of consequence. A risk assessment identifies and characterizes these risks. The model involves three stages—assess, change, and maintain.
The assessment stage is where risk assessments and gap analyses are performed. It’s important to establish areas and vectors, and determine potential targets. In the change stage, areas and vectors risks are mitigated to acceptable levels. The results of the changes need to be confirmed and have the security levels changed as required. In the maintain stage, a periodic assessment is performed, updates made, and the process is reviewed to make sure it remains current.
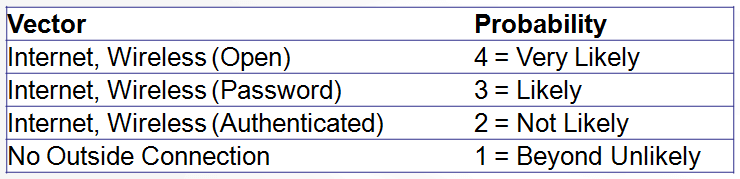
They presented a 4-square grid of likelihood versus consequence defining quadrants for low risk, moderate risk, and high risk. A scale was presented with probability—1 = beyond unlikely, 2 = not likely, 3 = likely, 4 = very likely and impact—1 = no impact, 2 = minor impact, 3 = major impact, 4 = severe impact. The model next considered probability vs. impact:
Next, impacts were viewed from the perspective of the public looking in, environmental considerations, personnel impact, and production impacts. Each identified risk item was evaluated and categorized in terms of probability and impact. Once these are fully fleshed out, the communications must include the connection to business considerations and get the required attention from the management team to build organization support for the changes required.
This framework provides an approach to reduce the fear and uncertainty and establish a concrete process for continuous risk mitigation. Randy and Greg closed by pointing to resources such as the U.S. Department of Homeland Security, your automation supplier and sales office, cyber security consultants and other session for the Emerson Exchange.
There is also an active thread on the subject in the Emerson Exchange 365 online community if you’d like to add your perspectives.