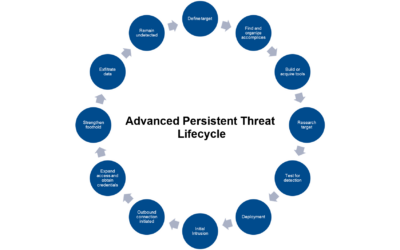
It is becoming increasingly clear that no organization is safe from cybersecurity risk. Operational technology (OT) assets are increasingly proving to be appealing targets for malicious entities, evidenced by many high-profile attacks in recent years. Further...
Cybersecurity
When Waiting for Rules Risks Everything
We all know cybersecurity is critical to safe and successful operation of our businesses. Moreover, most of us know that we could be doing more when it comes to cybersecurity. After all, we see new cyberattacks in the news almost every day, sometimes happening to...
The Sun Rises on New Cybersecurity Demands
Solar generation has been around for a very long time. However, until recently, it always made up a very small percentage of global power generation. As a result, solar generation was never really considered critical infrastructure. Today, however, that dynamic is...
Why Cybersecurity Looks Different in Life Sciences
We talk a lot about cybersecurity in the OT space. Cybersecurity has always posed a unique challenge for OT technologies, for a number of reasons. Often, OT teams are dealing with legacy technology that was never designed to be cybersecure and doesn’t operate in a...
Network Security Monitoring and NERC CIP
Emerson’s Nick Janouskovec presented NERC CIP-015-1 Internal Network Security Monitoring and Power and Water Cyber Security Network Security Monitoring at the 2025 Ovation Users’ Group Conference.
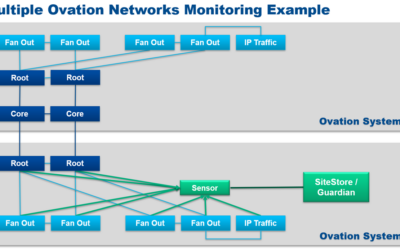
Dragos and Nozomi Network Security Monitoring
At the 2025 Ovation Users’ Group Conference, Emerson’s Thomas Kizer and Alejandro Cruz presented Network Security Monitoring Features and Functions Comparison: Dragos and Nozomi.
What Type of Cyber Defender Is Your OT Team?
We’ve talked a lot in this space about how cybersecurity is a particularly difficult challenge for OT teams. For decades, OT systems were specifically engineered to be closed to the outside world and from one another to ensure secure, reliable operation. That trend...
Stronger Together: Why Power Industry Cybersecurity Starts with Collaboration
One of the greatest challenges around the world is convincing people (or companies, for that matter) to make changes they don’t want to invest in. Regardless of the state of the marketplace, change that comes with added costs is always a difficult sell. And if that...
Protecting Critical Facilities from Cyber Attacks
A recent Forbes article,7 Steps Utilities Must Take To Protect Critical Facilities From Cyber Attacks highlights focus areas for manufacturers and producers to strengthen their operational resilience.
Upgrade or Get Left Behind: The Hidden Risks of Old Wireless Field Gateways
In a world where field operations depend on fast, reliable, and secure data transmission, sticking with outdated wireless field gateways can silently sabotage your performance. Legacy devices will still in operation, but they're often the weak point — exposing systems...
Unraveling the Cybersecurity Knot: How OT Teams Can Leverage Automation Experts
It has become increasingly obvious that the need for strong cybersecurity is not going to go away. Operational technology (OT) assets have increasingly become targets of both large-scale and small-scale attacks, often with devastating effects. OT teams need to be...
Industrial Cybersecurity Navigates a New Normal
Cybersecurity is a critical concern for industrial manufacturers these days, particularly as high-profile incidents targeting plants have become the new normal. No organization wants to risk the production loss, safety concerns, and reputation damage that come with a...
Keep Up to Date With the Latest News and Updates
Follow Us
We invite you to follow us on Facebook, LinkedIn, Twitter and YouTube to stay up to date on the latest news, events and innovations that will help you face and solve your toughest challenges.
Do you want to reuse or translate content?
Just post a link to the entry and send us a quick note so we can share your work. Thank you very much.
Our Global Community
Emerson Exchange 365
This blog features expert perspectives from Emerson's automation professionals on industry trends, technologies, and best practices. The information shared here is intended to inform and educate our global community of users and partners.