I’m in Orlando this week for the annual ARC Industry Forum. A large focus of today’s sessions is on Cybersecurity. The session, Cybersecurity – NIST and Automation Federation Updates on ICS Cybersecurity shared the current state of cybersecurity developments in the U.S.
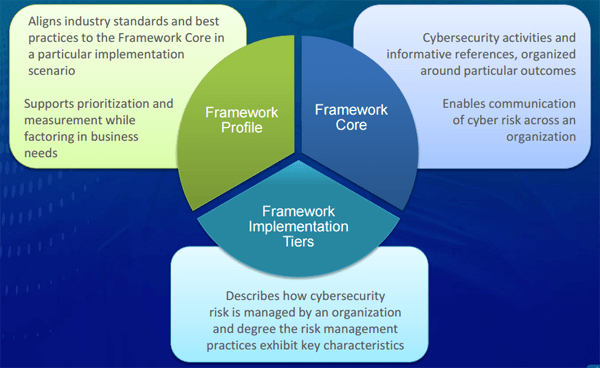
The panel opened with an overview of the NIST cybersecurity framework. The framework is for U.S. critical infrastructure which includes many of the process manufacturing and production industries. This framework was developed by the National Institute of Standards and Technologies (NIST) in collaboration with industry. Components include:
The framework provides guidance for managing cybersecurity risk including systems and assets, both physical and virtual. NIST established testbeds and test scenarios for continuous processes, discrete processes and distributed operations to research vulnerabilities and develop solutions to address.
Organizational training is a huge component in an effective cybersecurity program. Effective programs require technologies, people and processes. The way to think about the systems and processes is digital entropy. If there is not ongoing investment and support, they tend to disorder and risk levels increase. Safety and security are inextricably tied together. In a survey of cybersecurity and guidelines, the NIST framework was most broadly used and understood.
In the question & answer portion, a question came in about where to begin. There is a tremendous amount of guidance from NIST, ISA and others. From a NIST perspective, they are developing guidance for smaller and mid-size manufacturers on the top 5 cybersecurity recommendations for Operations Technology (OT)—primarily with the control system. Application whitelisting is the top recommended action.
Technological solutions without the creation of organizational cybersecurity awareness and ongoing training will not have the risk reduction sought.
One of the challenges is architecting the system which includes components from many suppliers. The largest suppliers tend to have better cybersecurity programs in their technology developments, project execution and lifecycle support services. Today, end users must bridge the differences but are pushing the smaller suppliers to embrace these cybersecurity frameworks.