Many factors contribute to maintaining a reliable and optimally performing control system.
Many factors contribute to maintaining a reliable and optimally performing control system.
This series will explore five essential P’s: Protection with Cybersecurity, Preventive Maintenance, Predictive Maintenance, Parts and Extended Warranty, and a Platform for Support and Lifecycle Updates.
Collectively, these elements form a simple but powerful framework to help safeguard your control system against downtime and improve your productivity.
We begin with:
PART I – PROTECTION WITH CYBERSECURITY
Cybersecurity protection of critical infrastructures is becoming of paramount importance as the lines between OT (Operations Technology) and IT (Information Technology) continue to blur in Industrial Control Systems. The attacks on the Colonial Pipeline, the discovery of Triton in the Middle East, and Stuxnet are all reminders that the threat looms large. Hence, implementing measures such as endpoint security, network segmentation, intrusion detection, access control, and security assessments is no longer optional in protecting your system from data breaches and unauthorized access, which could ultimately lead to operational disruptions.
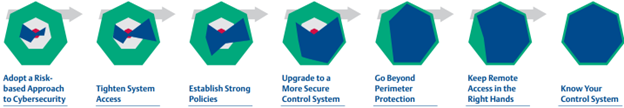
This Cybersecurity Guidebook for Process Control proposes the following measures to help you take the necessary steps to protect your assets against the next malware or ransomware attack:
- Adopt a Risk-based Approach to Cybersecurity – Become knowledgeable about where things could go wrong and your vulnerable points. Extend the operational and safety risk management processes to cybersecurity by working with experts to examine your network and control system setup. This type of assessment will help you prioritize security measures and resource allocation. It is also important to have a backup solution with onsite and offsite storage for recovery and to update your OT team’s cybersecurity incident response plan. These measures, while reactive, will help you get back to operations faster in case of any cyber incidents.
- Tighten System & Remote Access – Strict access controls must be enforced, including strong password management, multi-factor authentication, and role-based access authorization. Implementing the Principle of Least Privilege will help limit access to only what’s necessary for specific roles in the plant. Find ways to eliminate shared accounts that could be prone to password theft. It is also important to evaluate and design your remote access strategy with the proper permissions (view only vs.write access) and strong policies. Remote access should always be via the control system perimeter protection and jump servers for added security.
- Establish Strong Policies – Regular security awareness training will help educate your employees and stakeholders about the importance of cybersecurity and update them on the evolving best practices in the field. This will help arm your team with knowledge to recognize attacks, avoid unsecured practices, and report potential incidents before they can cause serious damage. Other policies, such as disabling USB ports or locking down workstations and servers within dedicated rooms and cabinets, will also minimize opportunities for both unsuspecting employees or even bad actors to compromise your security posture.
- Upgrade to a More Secure Control System – Applying security patches, new anti-virus signature files, and upgrading your software with updates or to the latest version can immediately address known vulnerabilities. Reputable control system vendors regularly review and test these patches for compatibility with your control system, mitigating risk to your operations. But while this is a recognized best practice, updates can often take the back seat to production issues and concerns. So consider automating patch management activities to eliminate the risk of running unprotected servers and workstations.
- Go Beyond Perimeter Protection – Network segmentation and firewalls provide a level of isolation between your critical ICS infrastructure and the business or other external networks. This separation can limit the impact of a security breach in one network and may prevent the lateral movement of malware (or cybercriminal access) to another. Deploying built-for-purpose firewalls at the control system perimeter will help you manage data flows and access to protect your system. Consider using controller firewalls to provide an additional layer of security within the control network, protecting controllers from message flooding and denial-of-service (DOS) attacks.
- Know Your Control System – Monitoring tools that can capture and analyze network traffic alert you of abnormal behavior, which could be due to cybersecurity threats or attacks. Active, continuous monitoring solutions such as Security Information and Event Monitoring (SIEM) can help improve your security intelligence and situational awareness by monitoring syslog events from firewalls, Windows events from workstations, and SNMP monitoring for your switches. You can gradually add more advanced Network Security Monitoring to achieve better visibility and detect advanced threats.
Key Considerations
Implementing effective cybersecurity measures can help ensure the continuous operation of your control system and the critical infrastructure it is running. Moreover, the right security protocols can help safeguard your data and intellectual property (such as formulas and recipes), personal information, and operational or financial data, which can lead to reputational damage if breached. Keeping abreast with good cybersecurity practices and enforcing them can also help you adhere to industry standards and government regulations.
However, having robust cybersecurity requires expertise that may not reside in the plant or involve collaboration between personnel in both IT and OT domains. The overlap in these areas can lead to some operational constraints, as controls and authentication may limit system access. Hence, the balance between security and operational efficiency must always be considered. Inevitably, there is also a cost that includes upfront investments in infrastructure and training, and long-term upkeep and subscriptions. The return on this investment must be clear and demonstrable to upper management.
So where should you begin?
Start with an Assessment
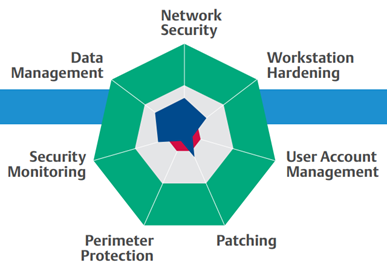
The guidebook above recommends that you start with a Cybersecurity Assessment. Plant and control system cybersecurity is not a “set once and forget” strategy but an evolving one. By conducting an initial assessment, you can understand the strength of your security controls, protocols, and defenses, allowing you to focus and prioritize your next steps considering your budget, risk tolerance, and operational constraints. Periodic succeeding assessments can guide your cybersecurity journey towards achieving and maintaining your desired overall cybersecurity posture for your system.
Author’s Note
While the solutions linked above are mainly for Emerson DeltaV control system users, the concepts and principles should generally apply to any other Industrial Control System. If you want to learn more:
- Partner with Emerson and Build the Right Cybersecurity Coverage
- The Future-proof, Secure, and Easy DeltaV Control System
- Cybersecurity for your DeltaV System