Juan Carlos Bravo
Mining & Power Industry Manager
This week, we heard in the news how the “Heart bleed” virus exposed sensitive information from millions of users and multinational companies across many industries. So this poses the question—how many miners are exposed to cyber-attacks. Very many indeed.
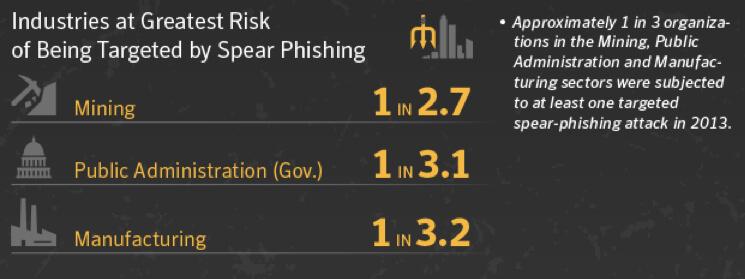
As reported in Mining Magazine’s January 29th article, Safe and Sound, Ernst & Young indicates that 41% of mining companies experienced an increase in external threats over the past 12 months.
What makes things even worse is that almost half of mining companies surveyed admitted that they do not have a proper security framework in place to mitigate and effectively manage these risks.
So why does the mining sector find itself at the center of this global issue?
As the miners play a more significant role in global, regional and local supply chains, a rising profile intensifies cyber threats. Furthermore, mining companies are top of the agenda for the increasing number of environmental activists promoting their own beliefs about a company’s operations.
Security for a mining company is a challenging undertaking. Security professionals must cope with isolated sites in locations often subject to geopolitical instability, where local infrastructure may be limited and the rule of law is sometimes lacking. In addition, mining companies have also inadvertently made a hacker’s job easier. Miners making big efforts to improve operational efficiency and reduce overheads have merged on one platform their information technology (IT) and operational technology (OT) systems.
Two systems that were once disparate have come together without the corresponding implementation of the security infrastructure required to protect it. OT systems are less secure and are less prone to attack. IT systems, despite their enhanced security, are more frequently targets of cyber-attacks. Combining both onto one platform could make the overall system more vulnerable, as OT’s security shortcomings are the gateway for hackers on the combined platform.
Furthermore, as companies seek to improve the sharing capabilities of their network and employees increasingly use their own devices to login to the shared network, the risk of attack is heightened.
Things will get worse before they get better. Even though mining companies are starting to place an increasing importance on communications and networks, threats are increasing due the growing need for automation and remote access to it. Like other process industries, the mining sector is facing challenges. Rising production costs and volatile commodity prices are forcing companies to exploit any potential operational efficiency. As miners attempt to improve productivity and reduce costs, the importance of automation grows. The world’s top mining companies have invested in new technology to run networks centrally, improving the consistency of both the production and maintenance of their sites.
This is especially the case for large players with operations around the globe. The business case is clear, but without the appropriate security framework, a stronger reliance on information technology increases a company’s vulnerability to cyber-attacks.
So what can we do?
A holistic security strategy should include how to confront and mitigate cyber attacks. Companies must regularly conduct attack tests, using data analytics to identify potential threats. Awareness is the key.
Companies must identify both hackers likely to attack and areas most vulnerable as targets, assessing where in current systems a breach is most likely to appear. They should invest in hardware that can be easily updated and maintained. Otherwise, hardware purchased today can become obsolete in just six months. A cyber-threat or attack response protocol should also be implemented. Above all, with hackers constantly looking for new ways to breach firewalls, innovation in communication and network security remains paramount.
I completely agree with this article, Cyber-hacking has become sophisticated and widespread activity and miners are in the front line of the battle. I also believe miners will be even more exposed when doing remote process control and remote monitoring of assets.
As explained in the article, miners will continue in the path of consolidating operations in a central location due the scarcity of qualified people and because of the economic benefits of doing so. That means performing remote process control of concentration plants to optimize the recovery rate will increase the exposure of confidential data. Therefore, miners will not just have to invest in a good infrastructure in order to do remote process control and remote monitoring but also in implement good cyber security work processes and practices.
That is why DCS supplies would have to work with customers and provide a platform that is easy to upgrade and monitor, provide a list of best cyber security practices and help them perform cyber security assessments of their systems. Suppliers and miners are in this together and it is in both their best interests that workers remain secure, production is not disrupted, and confidential information is not threatened.
This is a new era and attitudes are changing, cybersecurity is becoming more of a priority for miners and now they starting to thinking that cyber security is not a “set and forget” thing, but instead needs to be constantly monitored, maintained and evaluated.