Last month, a full day was devoted to the issues and practices around cybersecurity at the AFPM (American Fuel & Petrochemical Manufacturers) 2015 Q&A and Technology Forum.
Emerson’s Neil Peterson was one of the presenters. His presentation, The Myth of “Secure Out of the Box”, explored the expectation of process manufacturers and producers to have their automation vendors:…supply their Industrial Control Systems as “secure out of the box”. Industrial Control Systems have a significant number of built-in security capabilities plus additional services that can be implemented and configured based on security requirements of the asset owner. This presentation will provide insight into what is required from each party to get a system properly secured based on the risk environment of the system.
Neil opened with a cybersecurity minute reminding everyone that their process operations are only as secure as the weakest link. Systems are secure out of the box right up until you hit the power up button.
A huge challenge that many industries face, including refiners and petrochemical manufacturers, is that their plants are increasing in technical complexity. These plants are scaling larger and large, becoming more integrated complexes and have project teams spanning multiple Engineering, Procurement & Construction (EPC) and module suppliers. The capabilities of automation technologies are also accelerating.
For example, a large Olefins plants a few years ago was 800,000 tons/year. Now, 1.6M tons/year facilities are being built and plans are underway for 2M ton/year-sized plants. This means bigger equipment—10 years ago, 42″ valves were virtually unknown. Compressors are going from 60 megawatt units to 80, 90, 110 megawatt units.
At the same time, many regions of the world are experiencing a loss of expertise as members of the baby boom generation approach and reach retirement age. In other regions, there is a lack of experience where these facilities are being built.
Given these challenges, cybersecurity is yet another challenge. Even by specifying, “Must be IEC 62443 compliant” or “must be ISA99 compliant”, this will not assure compliance or security “out of the box”. Think about a PC at your home. It requires continuously updating anti-virus signatures, software patches, user access control, routers & firewalls and training to avoid opening untrusted attachments and hyperlinks. This is not “set and forget”.
For control systems with many secure capabilities embedded, it still takes effort to establish, use and maintain these capabilities using secure practices. Suppliers can help manufacturers and producers with risk assessments to that identify targets, assess threats, analyze access paths to targets and install compensating countermeasures. Network scans look for open ports, new or undocumented devices and rogue access points.
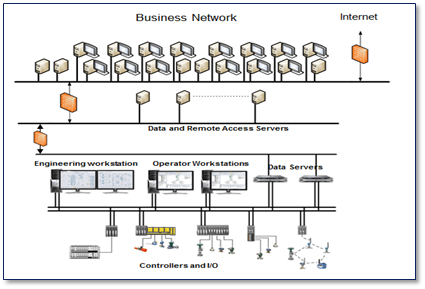 Control systems should be designed with secure network architectures, isolated from the plant or Enterprise network using a perimeter firewall or other security device. Neil noted that the DeltaV system uses separate physical network segmentation and is not dependent on the correct implementation of VLANs or other virtual network solutions to create the desired segmentation.
Control systems should be designed with secure network architectures, isolated from the plant or Enterprise network using a perimeter firewall or other security device. Neil noted that the DeltaV system uses separate physical network segmentation and is not dependent on the correct implementation of VLANs or other virtual network solutions to create the desired segmentation.
This isolation automatically occurs as part of the DeltaV system implementation – the user does not have to do it on each system. Since it enforces the use of a private, non-routing, Ethernet address space, a DeltaV network administrator cannot (accidentally) make a direct connection between the DeltaV network and the plant LAN or route outside the plant or facility.
Also, using a Demilitarized Zone or DMZ as a buffer from the plant/enterprise LAN provides an additional layer of security. A DMZ is used to buffer data and users so they never come directly to the control system from the plant/enterprise LAN. Finally, in an emergency (e.g. external malware attacks), the control system needs to be able to disconnect from the external LAN without affecting critical control functions.
Neil described several other technologies and practices that we’ll share in an upcoming post.
You can connect and interact with other cybersecurity and control system support experts in the Operate & Maintain group in the Emerson Exchange 365 community.





