At the upcoming October 14-16, 2019 AFPM Operations & Process Technology Summit, Emerson’s Eric Braun and Marcio Donnangelo will present on the subject of Industrial Internet of Things (IIoT) cybersecurity considerations. I’ll preview a few things from their presentation and invite you to join their session on Monday, October 14, at 11am if you plan to be in San Antonio, Texas.
Eric and Marcio will discuss the proven process to ensure cybersecurity for IIoT implementations and will describe the security mechanisms built into wireless industrial communications which can be used to protect IIoT implementations in plants and facilities. They will share the insights and experiences gained over the last dozen years in applying wireless, IIoT-based sensors. When used in combination with embedded operational analytics and shared in a timely manner with the right personnel, this actionable information can provide the insights and recommendations to improve safety, reliability and energy consumption.
When looking at the entire control and monitoring architecture, users can perform several actions to maintain their cyber defenses. These include keeping current on firmware and software revisions, training users in cybersecurity best practices, backing up and storing data securely, using secure communications protocols, limiting privileges only to what’s required for the role, logging actions with synchronized times, disabling unused functions and ports, and restricting physical access.
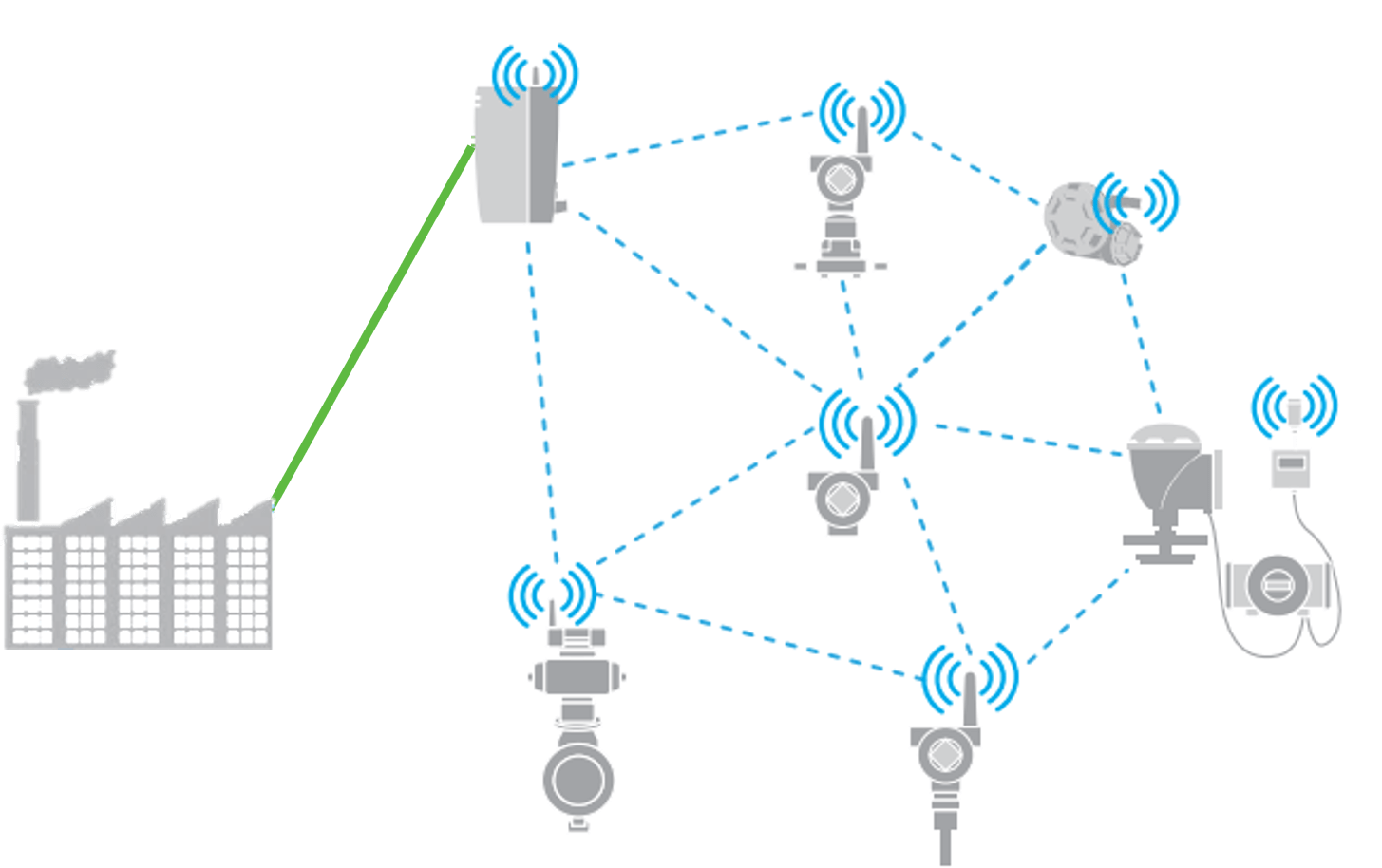 For the IIoT devices themselves, using secure protocols such as IEC 62591 WirelessHART is important. The sensors form a mesh network to communicate wirelessly back to a gateway connected by secure Ethernet, serial wired or Wi-Fi communication protocols to a control or monitoring-only system. The WirelessHART protocol uses encrypted messaging based on strong AES-128-bit encryption. Multiple levels of keys are used (join key, network key, session key, etc.) and the protocol supports key rotation.
For the IIoT devices themselves, using secure protocols such as IEC 62591 WirelessHART is important. The sensors form a mesh network to communicate wirelessly back to a gateway connected by secure Ethernet, serial wired or Wi-Fi communication protocols to a control or monitoring-only system. The WirelessHART protocol uses encrypted messaging based on strong AES-128-bit encryption. Multiple levels of keys are used (join key, network key, session key, etc.) and the protocol supports key rotation.
Firmware updates to these IIoT devices and wireless gateways are digitally signed to prevent tampering, and firmware upgrades require administrative access to perform. Users can upload their own security certificates to the gateway for an additional layer of defense.
Eric and Marcio will highlight additional defense-in-depth cybersecurity strategies including restricted, roles-based access; time synchronization and system log retention best practices; unused port and function closing/disabling; supplier security guidelines and recommendations for training, plus system hardening and configuration. It’s also very important to assess the suppliers’ security practices through the lifecycle of their technology and service delivery offerings.
Eric, Marcio, and the rest of the Emerson Refining & Petrochemical industry team look forward to seeing you in San Antonio to discuss your digital transformation initiatives and cybersecurity practices to maintain strong cyber defenses. Visit the Downstream Hydrocarbons section on Emerson.com for more on the technologies and solutions to drive business performance improvements in your facility.


