Many factors contribute to maintaining a reliable and optimally performing control system. This series will explore five essential P’s: Protection with Cybersecurity, Preventive Maintenance, Predictive Maintenance, Parts and Extended Warranty, and a Platform for Support and Lifecycle Updates.
ICS cybersecurity
Five Critical Controls for OT Cybersecurity
At the October Emerson Exchange conference in Texas, Dragos’ Robert M. Lee was a keynote speaker on cybersecurity practices. In his talk, Robert pointed to a new guide, 5 Critical Controls for World-Class OT Cybersecurity.
Growing Cybersecurity Threats and Mitigation Approaches Podcast
Emerson’s Director of Cybersecurity, Mike Lester, discusses with podcast host Jim Cahill many of the issues and growing threats companies face, as they try to maintain strong cybersecurity postures.
Maintaining Cybersecurity Strength
In a Plant Magazine article, ‘Cyber-securing’ your plant, Emerson’s Michael Lester joins other cybersecurity experts to share his thoughts on building and maintaining a strong cybersecurity posture
Foundational Principles in Cybersecurity
While no manufacturing organization can guarantee it will never be affected by one, there are foundational actions business and cybersecurity leaders can take to remove silos, operate holistically and implement best practices to reduce risk from these types of threats.
Teaming IT and OT on Cybersecurity
In a Refiner’s Guide to Digital Transformation article, No more silos: OT and IT team up to tackle cybersecurity, Emerson’s Rick Gorskie shares strategies on how to enhance collaboration and protection.
Sharing Cybersecurity Expertise
As the calendar shifts to November, I didn’t want to let the October National Cybersecurity Awareness Month go by without recapping some of the activities from the Emerson team.
ICS Cybersecurity in Digital Transformation Initiatives
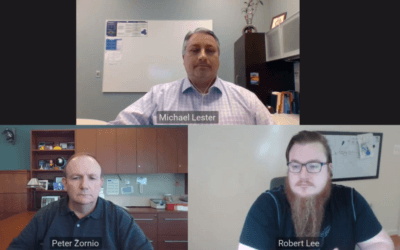
Emerson Automation Solutions CTO Peter Zornio & Director of Cybersecurity Michael Lester were joined by Dragos CEO Robert M. Lee to discuss cybersecurity in digital transformation initiatives. In the webinar, Enable a Secure Digital Transformation with your ICS, Robert, Peter and Michael discussed ways to deal with the challenges of an increased attack surface from increase connections and flows of data to a wider group of people.
Cybersecurity and Digital Transformation
On September 14, 1pm EDT webinar, Enable a Secure Digital Transformation with your ICS, Emerson Automation Solutions’ Chief Technology Officer Peter Zornio and Director of Cybersecurity Strategy, Governance & Architecture Michael Lester team up with Dragos CEO Robert M. Lee for a conversation on how to deal with these new challenges and implement a secure digital transformation.
Better Understanding Cybersecurity Webinar Series
Emerson’s Darren Greener hosts a series of seven webinars, Is now the right time to understand Cybersecurity? to help you better understand ways to design and apply robust defensive strategies for your Operational Technology environment involving people, processes and technologies.
Cybersecurity and Operational Technology at ConnectedPlant
One of the conferences for the power and chemical processing industries is the ConnectedPlant conference. The focus is on the technologies and solutions focused on improving plant operations. Some of the technologies explored included artificial intelligence (AI),...
Hardening Supply Chain Cybersecurity
The SANS Institute provides information security training and security certification for security professionals. They hold an ICS (Industrial Control System) Security Summit each year. At the 2019 ICS Security Summit, Emerson's David Foose presented Practical...
Keep Up to Date With the Latest News and Updates
Follow Us
We invite you to follow us on Facebook, LinkedIn, Twitter and YouTube to stay up to date on the latest news, events and innovations that will help you face and solve your toughest challenges.
Do you want to reuse or translate content?
Just post a link to the entry and send us a quick note so we can share your work. Thank you very much.
Our Global Community
Emerson Exchange 365
The opinions expressed here are the personal opinions of the authors. Content published here is not read or approved by Emerson before it is posted and does not necessarily represent the views and opinions of Emerson.