The Australian & New Zealand publication, Process Technology sought business thought leaders’ outlooks for 2022. Emerson’s Boris Gabin shared his thoughts.
cybersecurity
Take Better Control of Security with Integrated Patch Management
These days it seems as if we are hearing about new cybersecurity threats to industrial operations nearly every month. Whether it is a ransomware attack, an outage due to malware, or an attack via a new, unanticipated vector, the risks associated with a cyberattack can...
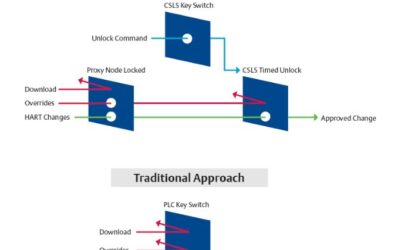
Defense-in-depth Approach Helps Prevent Unauthorized Changes in Safety Logic
One of the main concerns from users of process safety systems is how to effectively protect the SIS against unauthorized changes of the safety logic. The traditional protection approach is based on a key switch on the safety PLC; before somebody can alter the safety...
Maintaining Cybersecurity Strength
In a Plant Magazine article, ‘Cyber-securing’ your plant, Emerson’s Michael Lester joins other cybersecurity experts to share his thoughts on building and maintaining a strong cybersecurity posture
Episodio 33: Protección Cibernética en Sistemas Instrumentados de Seguridad
En este episodio el experto en Sistemas de Control y Sistemas Instrumentados de Seguridad, Sergio Díaz, nos comenta sobre las consideraciones más importantes en términos de ciberseguridad en los sistemas de las plantas. Hablamos sobre arquitecturas recomendables,...
Making Sense of Cybersecurity
It seems as though every week we’re alerted to a new cybersecurity breach impacting another industry. Unsurprisingly, organizations across the globe—particularly those in critical infrastructure such as power and water providers—are responding by quickly acting to...
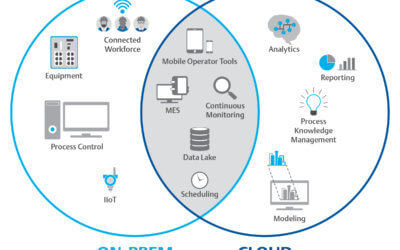
A More Measured Move to the Pharma Cloud
There is little doubt that the recent explosion in available cloud technologies has been a boon for manufacturing across a wide array of industries. Pharmaceutical manufacturers are no exception, and organizations are now carefully considering where leveraging cloud...
Integrated Control and Safety is More Valuable than Ever
There can be little doubt that COVID-19 has significantly changed the way we all work, and a key example of that change is a massive increase in remote connectivity across industries. In a recent Control Design article examining how COVID has altered the manufacturing...
Ovation Users’ Conference – It’s a Pleasure to be of Service
In an Ovation Users’ Conference panel discussion between Glenn Heinl, vice president of Lifecycle Services; Mike Brown, manager of lifecycle proposals; Jaime Foose, director of security solutions and lifecycle shared services; and Hugo Ibarra, manager of west regional...
Five Things You Can Do, Starting Today, to Improve Your Cybersecurity Defenses
Recent world events—from the expansion of remote access in response to COVID restrictions to high-profile industrial cyberattacks—have put a renewed focus on cybersecurity. While cybersecurity needs vary from organization to organization, there are common, critical...
Implementing Strong Cybersecurity Best Practices Reduces Cyber Risks
The importance of cybersecurity has escalated in response to remote work brought on by the global pandemic. Increased connectivity requires organizations to digitally transform operations to support a more sustainable, safer and healthier future. The recent intrusion...
Latest Ovation Release Improves Performance, Simplifies Troubleshooting and Provides Added Protections
Emerson’s industry-leading Ovation™ platform integrates digitally transformative software and technologies into a unified system that helps customers tackle their toughest challenges. Rick Kephart, Emerson’s vice president of technology for the power and water...
Keep Up to Date With the Latest News and Updates
Follow Us
We invite you to follow us on Facebook, LinkedIn, Twitter and YouTube to stay up to date on the latest news, events and innovations that will help you face and solve your toughest challenges.
Do you want to reuse or translate content?
Just post a link to the entry and send us a quick note so we can share your work. Thank you very much.
Our Global Community
Emerson Exchange 365
The opinions expressed here are the personal opinions of the authors. Content published here is not read or approved by Emerson before it is posted and does not necessarily represent the views and opinions of Emerson.